Azure MFA Fraud Protection
Even when Multi-Factor Authentication (MFA) is active, there’s still a risk of password compromise by malicious actors. This could occur, for instance, following a successful phishing campaign or if they gain access to a database of compromised accounts. Unknown MFA approval requests received by users could be the work of such actors who have accessed their passwords.

So, what can be done to counteract this? Today, I’m excited to share a feature I recently implemented on my Microsoft Azure Active Directory tenant: the Multi-Factor Authentication Fraud Alert. This feature adds an extra layer of security, enhancing user protection against unauthorized access and helping track fraudulent attempts.
What benefits does it bring? It empowers users to report unauthorized MFA notifications to the administrators. When a user flags an MFA prompt as suspicious, this event becomes visible in various reports, such as the sign-ins report, audit logs, and the risk detection report.
Here’s how it works: Imagine a cybercriminal manages to steal your password and attempts to log in to your account. With MFA activated, the criminal would encounter a second authentication request, like a prompt to enter the code displayed on your phone screen. If you see an authentication prompt on your phone when you’re not trying to log in, the Fraud Alert feature allows you to initiate a fraud alert. First, the user would indicate that the authentication request wasn’t initiated by them, and then they can report the prompt to the administrators.
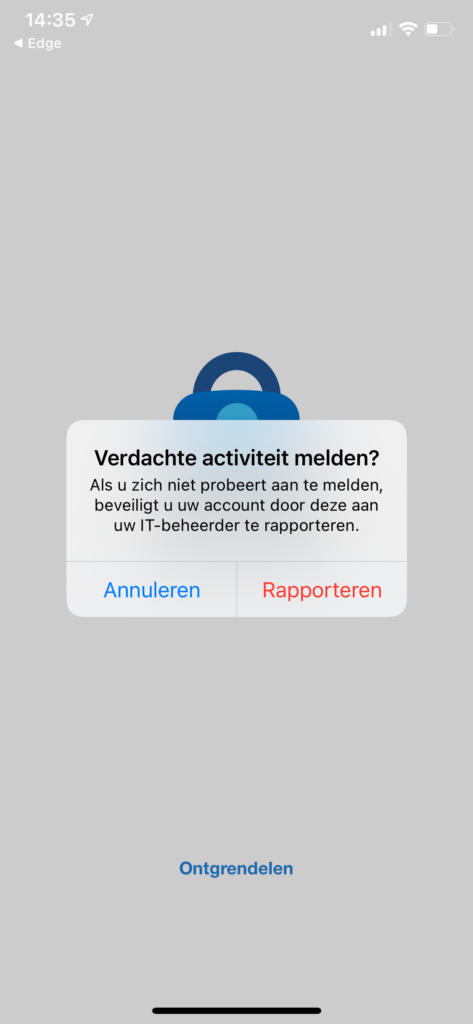
This function is available provided that your tenant includes a Premium license. You can find it by searching for the Multi-Factor Authentication section under your tenant. Within this section, look for Fraud Alert and click on it. You’ll see three options:
- Allow users to submit fraud alerts: this activates the feature I’ve described.
- Automatically block users who report fraud: this will automatically block users who send a fraud alert.
- Code to report fraud during initial greeting: a numerical sequence you can use to report an authenticated prompt.
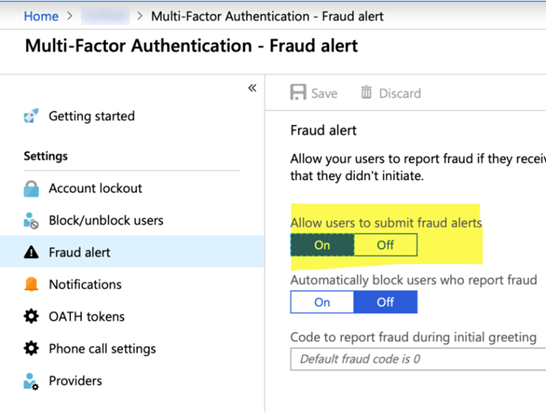
Administrators can also be notified upon fraud detection. You can set this up by navigating to Multi-Factor Authentication and then clicking on Notifications. Enter the email address where you’d like to receive reported prompts.
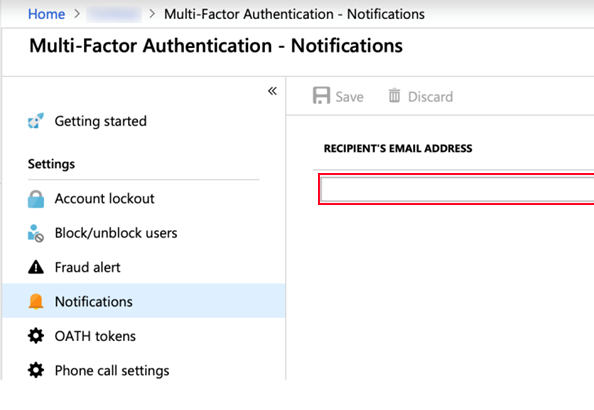
When an alert is made, the specified email will automatically receive a message from azure-noreply@microsoft.com with the subject line “Multi-Factor Authentication Fraud Alert”. The body of the email will specify the user involved, enabling the administrator to begin an investigation.
I hope you found this blog post both interesting and helpful.
For more information, please consult the following resources:
